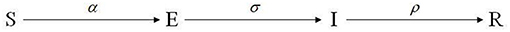- 1School of Statistics and Mathematics, Zhejiang Gongshang University, Hangzhou, China
- 2Academy of Zhejiang Culture Industry Innovation & Development, Hangzhou, China
- 3Department of Computer Science and Information Systems, University of North Georgia, Oakwood, GA, United States
- 4School of Tourism and Urban-Rural Planning, Zhejiang Gongshang University, Hangzhou, China
At present, rumors appear frequently in social platforms. The rumor diffusion will cause a great impact on the network order and the stability of the society. So it's necessary to study the diffusion process and develop the rumor control strategies. This article integrates three heterogeneous factors into the SEIR model and designs an individual state transition mode at first. Secondly, based on the influencing factors such as the trust degree among individuals, an individual information interaction mode is constructed. Finally, an improved SEIR model named SEIR-OM model is established, and the diffusion process of rumors are simulated and analyzed. The results show that: (1) when the average value of the interest correlation is greater, the information content deviation is lower, but the rumor diffusion range will be wider. (2) The increase of the average network degree intensifies influence of rumors, but its impact on the diffusion has a peak. (3) Adopting strategies in advance can effectively reduce the influence of rumors. In addition, the government should enforce rumor-refuting strategies right after the event. Also, the number of rumor-refuting individuals must be paid attention to. Finally, the article verifies the rationality and effectiveness of the SEIR-OM model through the real case.
Introduction
With the rapid development of Internet information technology, information diffusion has become more and more convenient. However, due to malicious tampering and other reasons, information will continue to be alienated in the diffusion process, which will increase its complexity and redundancy. While receiving a large amount of information, netizens cannot verify its authenticity and accuracy. This provides an opportunity for the large-scale rumor diffusion. At this time, if the hot information related to the national economy and people's livelihood is tampered with and not controlled in time, it will easily breed public anxiety, panic and other emotions, which will bring great economic impact to individuals, society or the country, and even threaten the harmony and stability of society. For example, when COVID-19 broke out at the end of 2019, rumors that “masks cannot prevent viruses” diffuse on social platforms in many countries, thus many people failed to take correct epidemic prevention measures in time, causing the widespread diffusion of COVID-19 in many countries, which greatly affected the social and economic development in the world. As a result, analyzing the rumor formation, diffusion and its control strategy has an important theoretical and practical significance.
Scholars have conducted a lot of research on the diffusion and control of rumors and have achieved some results. At present, the research on rumors is mainly divided into two categories: (1) A qualitative analysis of the diffusion process of rumors from the phenomenon itself, mainly to study its causes and counter measures. However, most of these studies lack specific empirical investigations and quantitative methods, and their conclusions are subjective; (2) Use evolutionary game theory, communication dynamics and other related methods to construct mathematical models, and use mathematical derivation or computer simulation to achieve inter-group interactive simulation of information diffusion, and observe the results to explore the rules of rumor diffusion and counter measures.
However, most of these models simulate the diffusion process of rumors, but rarely consider the formation of rumors and psychological influence factors. Based on this, this article integrates the individual's diffusion willingness, the individual's forgetting degree, and the intensity of government punishment into the SEIR model, and designs a state transition mode at first. Secondly, it considers the individual's decision-making behavior in the process of rumor generation and diffusion, and establishes information interaction mode among individuals. Finally, an improved SEIR model named SEIR-OM model is established. Also, rumor generation and diffusion process are simulated and analyzed from two aspects: model parameter setting and rumor control strategy.
The structure of the article is organized as follows: section Literature Review is a literature review. Section Research Framework builds a SEIR-OM model. Section Model Construction simulates the rumor evolution process through simulation experiments, and studies the influences of model parameters and different rumor control strategies on the rumor evolution. Section Simulation Experiment validates the SEIR-OM model with the real case from the imported food safety issue during the COVID-19 Pandemic. Section Empirical Analysis makes the conclusions and prospects for future work.
Literature Review
This section reviews the relevant literature from two aspects: rumor diffusion and control.
With regard to the research on the rumor diffusion, most of the existing literature uses infectious disease models and evolutionary game models to analyze their diffusing process: (1) the first aspect is the research on the dynamics of rumor diffusion based on the infectious disease model. For instance, Zhang and Zhu (1) studied two kinds of rumor diffusing dynamics with quadratic relationship by establishing the I2S2R model, and concluded that the diffusing intensity of second rumors depended on the diffusing intensity of initial rumors. In addition, based on the SIR model, Huang and Jin (2) divided the immunized population into two categories: those who accepted rumors but were not interested in diffusing them, and those who did not believe rumors, and analyzed two strategies through numerical simulation: random immunization and target immunization. The results showed that the application of random or directed immunity could effectively prevent the diffusion of rumors while reducing the credibility of rumors. Jiang and Yan (3) proposed a piecewise SIR model to quantify the diffusing speed, scale and influence of online information. The simulation results showed that there was no proportional relationship between the sustained influence of a message and the number of diffusers. Zhou et al. (4) analyzed the influence of network topology on rumor diffusion based on SIR model. The mean field analysis showed that the number of infected nodes depended on the network topology. Moreno et al. (5) studied the dynamic process of rumor evolution in homogeneous network and scale-free network. The results showed that when rumor diffused in the latter, the number of people who did not diffuse rumor in the final state had nothing to do with the degree of the source of infection, but was closely related to the probability of infection. Zhang et al. (6) considered the influence of the attractiveness of information itself on the diffusion, and based on this, they proposed a rumor diffusion model based on the diffusion ability. Most of the above-mentioned literatures have added more diverse individual states on the basis of classic infectious disease models. However, since the individual interaction mechanism in the process of rumor diffusion is not considered, most studies still use fixed reception probability to describe the process of individuals receiving external information. (2) The second aspect is to use the evolutionary game model to describe the game decision-making process of individuals facing rumors. For instance, Fernández-Domingos et al. (7) established a prisoner's dilemma game model, and analyzed the behavior of each node in the topology during network information diffusion. This study showed that in small-scale networks, choosing cooperation was the optimal strategy of nodes. On the contrary, for large-scale networks, choosing non-cooperation was the optimal strategy. Furthermore, by using three real social network datasets, Li et al. (8) found that increasing the judgment ability of individuals could curb the diffusion of rumor effectively. Moreover, there existed some optimal risk coefficients and punishment fractions that could help more people refuse to diffuse rumor. Mojgan et al. (9) proposed an evolutionary game model to analyze the diffusion process of rumors in social networks. The model studied the factors affecting people's decision-making, such as social anxiety, and conducted sensitivity analysis experiments to illustrate the impact of different factors on the process of rumor propagation. The analysis showed that people's attitude toward rumor/anti-rumor had a significant impact on rumor diffusion. In addition, factors such as social anxiety and rumor intensity also accelerated the rumor diffusion. Most of the above-mentioned documents have studied the diffusion process of rumors among individuals on the Internet, but rarely studied the process of their formation, which cannot fully reflect the large-scale diffusion process of rumors from its initiation, and from weak to strong of the whole evolution. However, the research on the formation mechanism of rumors can effectively reduce the generation of rumors, which is very important for rumor control. Therefore, it is necessary to study the formation mechanism of rumors.
In addition, regarding the research on rumor control, the methods used in the existing literature mainly include controlling high-influence nodes, controlling key connecting edges, and diffusing refuting information. The details are as follows: (1) Control high-influence nodes. This type of method aims to find nodes that contribute to the rumor diffusion, and then delete such nodes to reduce the influence of rumors. Some typical literature is as follows: based on a variety of complex network metrics of network centrality, e.g., centrality of degree, intermediate, proximity, etc., Comin et al. (10) analyzed three communication mechanisms and provided an effective method of hairstyle communication sources. Inspired by the idea of gravity formula, Ma et al. (11) took the k-shell value of the node as its mass and the shortest path length between the two nodes as the distance, proposed the gravity centrality method to determine the high influence node, and compared it with other centrality indexes. (2) Control key connecting edges. This type of method aims to find the edges that play key nodes in information dissemination and delete them to reduce the rumor diffusion. Some typical literature is as follows: Pallis (12) deleted k edges from the original network to diffuse rumors as little as possible, and explained which edge should be deleted depended on the eigenvalues of the network adjacency matrix. Yuan et al. (13) proposed a fine-grained heuristic algorithm to solve the rumor propagation minimization problem. The experiment showed that the heuristics based on betweenness and out-degree were orders of magnitude faster than the greedy algorithm in terms of running time. (3) Diffusing refuting information. This type of method diffuses information that is contrary to the content of the rumors, so that as many nodes as possible are not deceived by the rumors. Some typical literature is as follows: Zhang et al. (14) presented an in-depth analysis of the function of official rumor-refuting information (ORI) in suppressing and quashing rumors. They determined the influencing factors and constructed a competition model. The simulation results also indicated that government credibility and the release time of ORI played a critical role in controlling rumors. Zhang and Xu (15) presented a simple model to describe the interplay between rumors and rumor-refuting information based on biomathematics theory. By drawing from differential equations, a theoretical analysis reveals that this model exhibited three dynamic cases: extinction of rumors, extinction of rumor-refuting information and coexistence. Also, they studied the stability of the equilibrium points of three cases, found that stable condition of equilibrium point, and showed unstable case of model. Most of the above-mentioned literature studies the effects of different rumor control strategies adopted after the occurrence of hot events, but few literature explores the role of rumor prevention strategies adopted before the occurrence. However, proactive prevention strategy is also an important part of rumor control strategy, so it is necessary to study it.
To sum up, the academies have conducted a certain depth of research on the diffusion and control of rumors, but there are still deficiencies. Based on this, in section Model Construction, this article first designs a state transition mode based on SEIR model. At the same time, considering the rumor generating factors such as information tampering and individual heterogeneity factors such as personal reputation, an information interaction mode is constructed. Finally, SEIR-OM model is constructed by fusing state transition mode and information interaction mode. In addition, this article also divides the rumor control strategy into proactive strategy and reactive rumor refutation strategy, and analyzes their effects through simulation experiments.
Research Framework
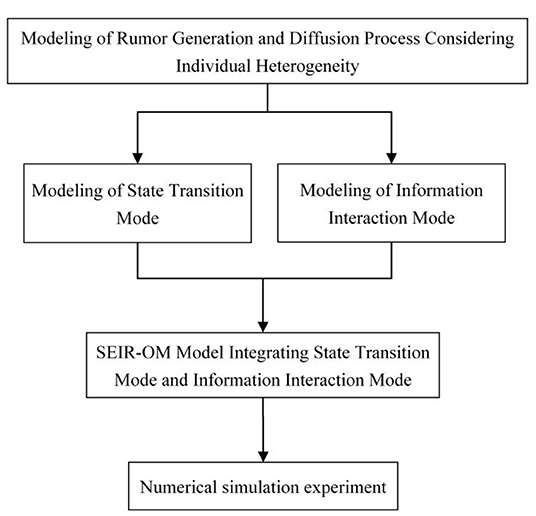
This article integrates the individual's diffusion willingness, the individual's forgetting degree, and the intensity of government punishment into the SEIR model, and designs the state transition mode at first. Secondly, it refers to the trust theory and information asymmetry theory, considers the main factors affecting information interaction among individuals, and establishes information interaction mode. Finally, an improved SEIR model named SEIR-OM model is constructed, and its formation and diffusing process are simulated and analyzed from two aspects: model parameter setting and rumor control strategy. The framework of the article is shown in Figure 1.
Model Construction
Classic SEIR Model
SEIR model is a classical infectious disease dynamics model, which is often used in the medical field to simulate the transmission process of infectious diseases (16, 17) and predict the development trend of epidemic situation (18, 19). The dissemination of public opinion information needs go through the process of germination, development, outbreak and finally decline, which is highly similar to the whole process of the development of infectious diseases. Therefore, in the existing research on information dissemination, a considerable proportion of studies uses SEIR model to analyze information dissemination.
The classic SEIR model divides individuals into four categories according to their different states in the diffusion process, namely: uninformed individual S, silent individual E, communication individual I, and immune individual R. Among them, uninformed individuals represent those who have not received information, corresponding to those who do not know the public opinion information in reality, and the initial states of most individuals are uninformed states; silent individuals represent those who have received information but have not diffused to uninformed ones; communication individuals represent those who receive information and diffuse information to other ones; immune individuals represent those referring to individuals who are no longer interested in information related to the event, which are the final states of individuals.
Moreover, the classic SEIR model has four assumptions: (1) The number of individuals always remains a constant, i.e., S+E+I+R=N (N is a constant); (2) Uninformed individuals turn into the silent after receiving information from the communication individual. Therefore, at t + 1, the number of newly-added silent ones is proportional to the number of communication ones at time t, and its proportional coefficient α is defined as the reception coefficient; (3) The number of newly-added silent ones at t + 1 is proportional to the total number of silent ones at time t, and its proportional coefficient σ is defined as the diffusing coefficient; (4) The communication individuals turn into immune ones after losing interest in the event-related information. Therefore, at time t + 1, the number of newly immunized individuals is proportional to the number of communication ones at time t, and the proportional coefficient ρ is defined as the immune coefficient. Based on the above four assumptions, the differential equations of the SEIR model are shown in formula (1):
Figure 2 is a schematic diagram of the classic SEIR model:
SEIR model uses fixed probability to describe the individual state transition process and information interaction process in the process of rumor propagation, ignoring the influence of individual heterogeneity factors on the process of rumor propagation. Based on this, next section will improve the classic SEIR model and construct the SEIR-OM model.
SEIR-OM Model Construction
In this section, the construction process of SEIR-OM model will be described in detail. The parameters and variables involved in the model are shown in Tables 1, 2.
State Transition Mode
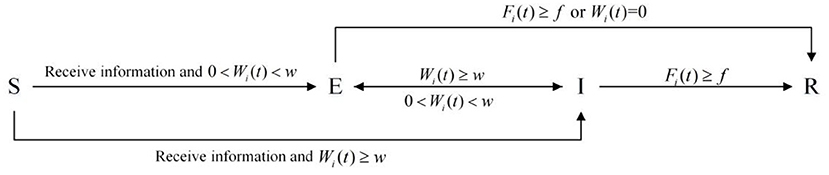
The SEIR model uses a fixed probability to describe the transition of an individual's state, without considering the heterogeneity of the individual, so it cannot explain the internal mechanism of the individual's state transition. Based on this, the individual state transition mode of the SEIR model is improved here, and two factors describing individual heterogeneity are introduced, namely: individual's diffusion willingness and the individual's forgetting degree, which are used as the conditions for individual state transition.
(1) Individual's diffusion willingness. Diffusion willingness refers to “the sending intensity of sender's personal consciousness” (20), which is used to determine whether the individual diffuses the information to the outside world. It is important to determine whether the information can be diffused on a large scale in social networks. Generally, the factors that affect the one's diffusion willingness include two aspects: one is the degree of interest correlation between the individual and the event, which refers to the degree of influence of the occurrence and development of an event on a certain aspect of the person's interests (21), e.g., the occurrence of public health emergencies will damage the personal interests of local residents. The higher interest correlation of the individual to the event indicates the stronger willingness to diffuse relevant information; the other is accumulated gains due to external feedback after the information diffusion. If other individuals receive the information diffused by this individual, this individual's diffusion gains will increase, and his willingness to diffuse the information will be stronger. However, if other individuals reject the information diffused by the individual, his/her diffusion gains will decrease, and the corresponding diffusion willingness is also weaker. Therefore, the individual's diffusion willingness Wi is described by formula (2) (22):
where bit = bi(t−1) + 0.1vit. Because each individual has a difference in the degree of interest correlation to a certain event, we assume that bi0 obeys a normal distribution with a mean value of μb and a variance of b2, and is mapped to the interval [0,1]. mi0 = 1, when other individuals receive the information sent by individual i, and mi is increased by 1.
(2) Individual's forgetting degree. Individual's attention to hot events will decay over time. Ebbinghaus research found that the failing of people's memory is fast at first and then slower. Considering that the degree of interest between individuals and the event will affect their attention to the event, referring to the Ebbinghaus forgetting curve equation, the individual forgetting degree Fi is described by the formula (3):
Similar to the classical SEIR model, SEIR-OM model also divides individuals into four categories: uninformed individuals S, silent individuals E, communication individuals I, and immune individuals R. They also have the same meaning as the classical SEIR model.
In the individual state transition mode, the state transition rules are set as follows: when an uninformed person interacts with a communication one, the uninformed individual will transform into a silent one or a communication one according to his diffusion willingness. When the silent individual's diffusion willingness is greater than or equal to the diffusion threshold w, it turns into a communication one. When a communication individual's willingness is less than the diffusing threshold w and >0, he/she turns into a silent individual. If the individual's diffusion willingness is <0 or the forgetting degree is greater than forgetting threshold f, he/she turns into an immune one. The individual state transition rule is shown in Figure 3.
Note that although uninformed individuals and immune individuals do not participate in information dissemination, there are some differences between them. The uninformed individual means that the initial state of most individuals is uninformed state. After receiving the information, the state of the uninformed individual will change. On the contrary, the silent individual means that the final state of most individuals is silent state, and it will not change again. Also, the silent individuals will disconnect from other individuals.
Information Interaction Mode
The large-scale rumor diffusion is inseparable from the information interaction among individuals, and the information interaction process includes two stages, namely: the receiving stage and the diffusion stage of information. Existing studies mostly use SEIR model and evolutionary game model to describe this process. However, the SEIR model describes this process through fixed reception probabilities and diffusion probabilities, ignoring the influence of individual heterogeneity factors on the information interaction process. While in the evolutionary game model, individuals choose whether to receive and diffuse information only based on the diffusion benefits. In addition, both the SEIR model and the evolutionary game model only describe the diffusion process after rumors are generated, and do not consider the rumor generation mechanism. Based on this, an information interaction mode is designed here to reflect the process of rumor generation and information interaction.
Information Content Deviation
Different people have different positions and opinions on the same public opinion event, and there are situations in the network where individuals distort and fabricate real information to gain attention. Therefore, in the process of information diffusion, information deviation is often caused, and a variety of different content of information coexist. In order to differentiate the information content mastered by different people and describe the difference between them and the original information content, the information content deviation set is established according to the Chinese sentence structure here.
In the Chinese context, a sentence is mainly composed of five parts, namely: subject, predicate, object, attributive, and adverbial. Therefore, the information content deviation set in the article is also composed of these five parts. Set the deviation set of the information grasped by the individual and the original information Di = < d1i, d2i, d3i, d4i, d5i >; the deviation set of the information content diffused by the individual and the original information Si = < s1i, s2i, s3i, s4i, s5i >. Among them, d1i, d2i, d3i, d4i, d5i, s1i, s2i, s3i, s4i, s5i are all described by values mapped to the interval [0,2]. d1i, d2i, d3i, d4i, d5i, s1i, s2i, s3i, s4i, s5i <1 means negative deviation, d1i, d2i, d3i, d4i, d5i, s1i, s2i, s3i, s4i, s5i <1 means positive deviation, d1i, d2i, d3i, d4i, d5i, s1i, s2i, s3i, s4i, s5i = 1 means it is consistent with the original information.
Factors Affecting Information Interaction Among Individuals
This section quantifies the two factors that affect the information interaction between people: one is the degree of trust between individuals and the other is the individual's mastery degree of event-related information.
(1) The degree of trust between individuals. Existing research on trust theory (23–25) generally believes that “trust is the premise of information exchange between individuals and the cornerstone of social networks. If there is no interpersonal trust, social networks will collapse.” Taking the convenience of social networks into account, it can make two netizens who are not related in real life communicate, but the degree of mutual understanding of the interactive dual is not high. This leads to the fact that netizens in social networks can only determine whether to trust each other through their social influence and the strength of the relationship between netizens. Based on this, the degree of trust between individuals is determined by the individual's social influence and the strength of the relationship between them.
(1) Individual's social influence. A person's social influence refers to his/her ability to influence other ones' behaviors in a social network, and reflects the importance of an individual in the network. In complex network theory, tightness can be used as a measure of node centrality, which is defined as the average shortest path from a node to other reachable nodes. Generally, the higher the tightness is, the more important the node is. Therefore, the individual's tightness formula in the complex network is used to calculate the individual's social influence Ii, as shown in formula (4):
(2) Strength of relationships among individuals. In reality, people tend to trust their close friends more and trust the information they convey. Therefore, the strength of the relationship between individuals will have an impact on information diffusion, i.e., the closer the relationship between individuals is, the higher the degree of mutual trust is. Here, the concept of individual embedding degree (26), i.e., the number of common neighbor individuals that two individuals have in the network, is used to describe the strength of the relationship between these two individuals, as shown in formula (5):
where ki-1 represents the number of neighbors remaining for individual i except for individual j. (ki-1) + (kj-1) represents the maximum number of common neighbor individuals that may exist between individuals i and j. In addition, the premise of setting the interaction between two entities is that they have a direct connection in the network. Therefore, when ki = kj = 1, it means that individuals i and j are each other's exclusive neighbors, and the relationship between the two is the strongest, i.e., Rij = 1.
In summary, the calculation of the trust degree Cij of individual i to individual j is shown in formula (6):
(2) The individual's mastery of event-related information. In social networks, only a small number of people can grasp more comprehensive information, while the vast majority only grasp part of the information and make behavioral decisions based on the limited information they have. This is called information asymmetry. The phenomenon of information asymmetry is an important driving force for the rumor diffusion (27). At present, the development of the Internet has made information acquisition more and more convenient, and the asymmetry of information between individuals will be weakened. However, at the same time, it will aggravate the level of information confusion in social networks. This is because the unique free speech space of the Internet allows any information to be diffused on a large scale in a short period of time, but it costs longer time to verify the information authenticity. Therefore, although the public have more opportunities and channels to obtain information, they cannot accurately judge the authenticity of the information, which further strengthens the asymmetry of individuals in terms of information accuracy. Based on this, this article introduces the individual knowledge reserve (28) and the degree of confusion in external information (29) to describe the individual's mastery of event-related information.
(1) Individual knowledge reserves. Because most individuals do not know the true situation of public opinion events, they can only judge whether to accept external information based on their own past experience and relevant knowledge. For example, during the outbreak of COVID-19, it was widely diffused on the Internet that dual yellow oral liquid could prevent virus infection. In fact, dual yellow oral liquid cannot prevent COVID-19 virus. However, due to the lack of knowledge of pathology and virology, the public chose to believe this information, which once triggered a panic buying wave. Based on this, the individual knowledge reserve Ki is assumed to follow a Poisson distribution with a mean value of λ to reflect the phenomenon that only a small number of individuals in the network have a relatively professional knowledge reserve.
(2) The degree of confusion in external information. After the diffusion of information, individuals gradually are aware of information with different contents. A large amount of redundant information will interfere with their judgment of the authenticity and accuracy of the information, so that there is a greater probability of accepting rumors or rejecting real information. Here, the degree of confusion in external information Σi is calculated by formula (7), as follows:
In summary, the individual's mastery of event-related information Gi is described by formula (8).
Information Interaction Mechanism
When the information receiver has a high degree of trust in the communication individual, he/she will accept the information sent by the communication one. In addition, the communication ones are divided into ordinary communication individual O and malicious communication individual M according to diffuse intention. Among them, the ordinary communication individual diffuse information that he/she believes to be true to uninformed ones, who will not tamper or process the information in the processing of information diffusion. The malicious communication ones tamper and process the information for gaining attention and increasing influence, and diffuse processed information to others. Since the information receiving mechanism of all individuals is the same, and the information diffusion mechanism of different communication individuals is different, the information reception mechanism of the individual must be set first, and then the information diffusion mechanism of the general and the malicious communication individual must be set separately.
(1) Individual information reception mechanism
When a communication individual sends information to neighbors, the recipient of the information compares the communication individual's trust level with his/her own trust threshold at first. If the former's reputation is greater than the trust threshold, the information will be accepted by the information recipient, and vice versa. After receiving the information, the information recipient updates the content that he/she believes to be true according to his/her mastery of the event-related information. The specific reception mechanism is as follows:
When Cij ≥ ci
When Cij < ci
(2) Information diffusion mechanism of ordinary communication individuals
Generally speaking, while diffusing information to the outside world, ordinary communication individuals will directly diffuse the information they believe to be true to other individuals, i.e.,
(3) Information diffusion mechanism of malicious communication individuals
Before diffusing information externally, malicious communication individuals will tamper with the information they believe to be true to a certain extent, and diffuse the tampered information to others. The degree of tampering will increase with the increase of the gain from the feedback of the tampered information, and decrease with the increase of the punishment of rumors. Therefore, the formula for calculating the tampered intensity Δi is as follows:
Information diffusion mechanism of malicious communication individuals is as follows:
where β is a random number of either 0 or 1.
Framework and Simulation Steps of SEIR-OM Model
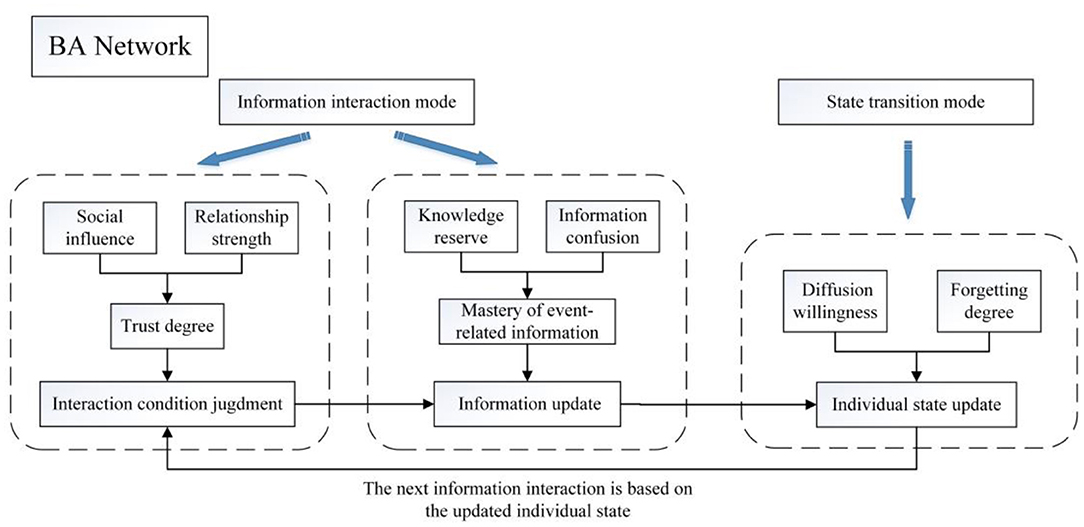
Based on the Barabási-Albert scale-free network (BA network) (30, 31), the Monte Carlo simulation method based on multi-agent is used to simulate the SEIR-OM model. Its construction process is shown in Figure 4.
Compared with the classical SEIR model, the state transition mode in SEIR-OM model can more reasonably and carefully describe the psychological mechanism of individual state transition. The information interaction mode in SEIR-OM model can not only distinguish different information contents, but also reflect the individual's psychological decision before receiving (transmitting) information.
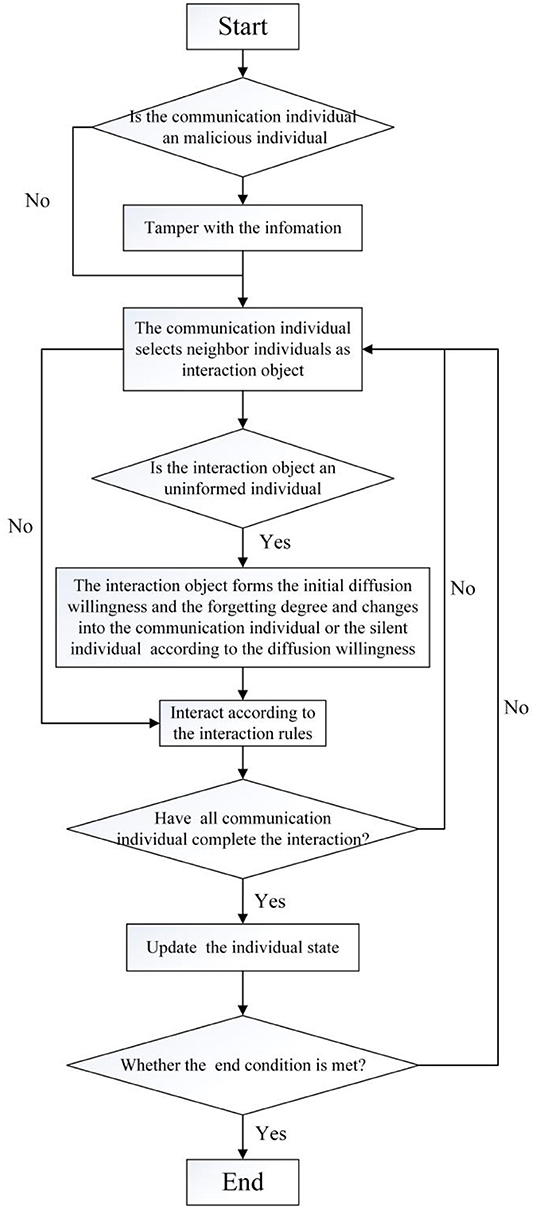
The specific process of the formation and diffusion of rumors is as follows:
(1) At the initial moment, a certain number of malicious communication individuals and general communication individuals are randomly generated, and their initial diffusion willingness and the forgetting degree of public opinion events are generated according to formulas (1) and (2), respectively.
(2) At any time, the communication individual i randomly selects its neighbor individual j as the object of information interaction. If the trust degree of i is greater than or equal to the trust threshold of j, information interaction is carried out according to the state of j. Generally, there are the following two situations: (1) If j is an uninformed individual, he/she will fully accept the information diffused by i, form the initial diffusion willingness and the initial forgetting degree, and transform it into a communication individual or a silent individual according to the initial diffusion willingness. (2) When j is a silent individual or a communication individual, the communication individuals i and j exchange information according to the formulas (9–13). If the trust degree of the communication individual i is less than the trust threshold of j, they will not exchange information.
(3) At any time, after all communication individuals have completed their outward communication, they update the individual's diffusion willingness, forgetting degree, and individual state in the network.
(4) Determine whether the end condition is met. The conditions for ending the interaction are set as follows:
(5) If the interaction end condition is not satisfied, repeat steps (2)–(4) until formula (14) is satisfied, and the interaction process ends. The specific process is shown in Figure 5.
Simulation Experiment
This section uses the Monte Carlo simulation method based on multi-agent system to explore the influences of model parameters on the process of rumor diffusion and the implementation effects of different rumor control strategies. The simulation network is constructed with BA network, and the individual scale in the network is set to 300.
The Influence of Model Parameters on the Process of Rumor Diffusion
This section starts with the model parameters and analyzes its influence on the diffusion process of rumors. There are 2 comparison indicators used in the analysis:
(1) Entire network information content deviation: it refers to the average value of the deviation between the information content in the network and the actual information content. Here, the deviation devi(t) between the information content diffused by the individual i and the real information content is set. The calculation is shown in formula (15), and the calculation of the deviation of the entire network information content deviation is shown in formula (16).
(2) Rumor diffusion range: it refers to the proportion of individuals holding rumors in the network to the total number of individuals on the network. Here, information with content deviation >0.5 is identified as a rumor, and the calculation is shown in formula (17). Based on this, the calculation of the rumor diffusion range is shown in formula (18):
The Impact of μb on Rumor Evolution Process
The mean value of the degree of interest correlation between all individuals and public opinion events μb will affect the individual's attention to the event, and thus have an impact on the diffusion of event-related information. Here take μb as 0.1, 0.3, 0.5, 0.7, and 0.9, respectively, for comparison. The results are shown in Figure 6.
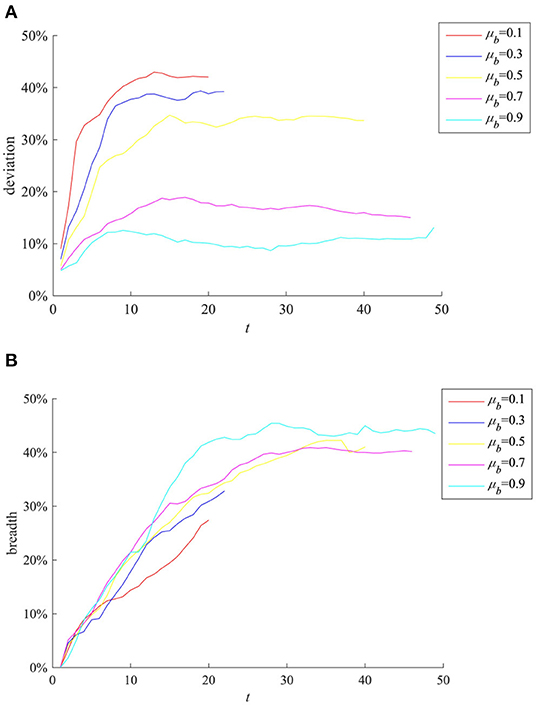
Figure 6. The impact of μb on rumor evolution process. (A) Entire network information content deviation. (B) Rumor diffusion range.
It can be seen from Figure 6A that as μb increases, the entire network information content deviation decreases. This shows that when the event is related to the interests of most individuals, they are more concerned about the authenticity of the information and more cautious about the information sent by the outside world, so that the entire network information content deviation of the entire network is lower. It can be seen from Figure 6B that as μb is larger, the rumor costs longer time to diffuse and its diffusion range is wider. This shows that individuals are more concerned about the incident and have a stronger willingness to forward information related to their own interests, and protect their own interests by expanding the influence of the incident, which also provides opportunities for the rumor diffusion and makes more widespread.
The Impact of Network Structure on Rumor Evolution Process
Social networks provide channels for information diffusion. If the network structure changes, the strength of relationships among individuals will change accordingly, which will affect the reception and diffusion of information. In order to study the influences of different network structures on the process of rumor diffusion, this section changes the value of h (h ∈ [0,N]) (Note that the BA network used in the simulation experiment is based on an interconnected network, after the introduction of several new nodes. The new nodes will be connected to h existing nodes). Our experiments generate BA networks of different structures, and compare the rumor diffusion under different network structures, then the results are as shown in Figure 7.
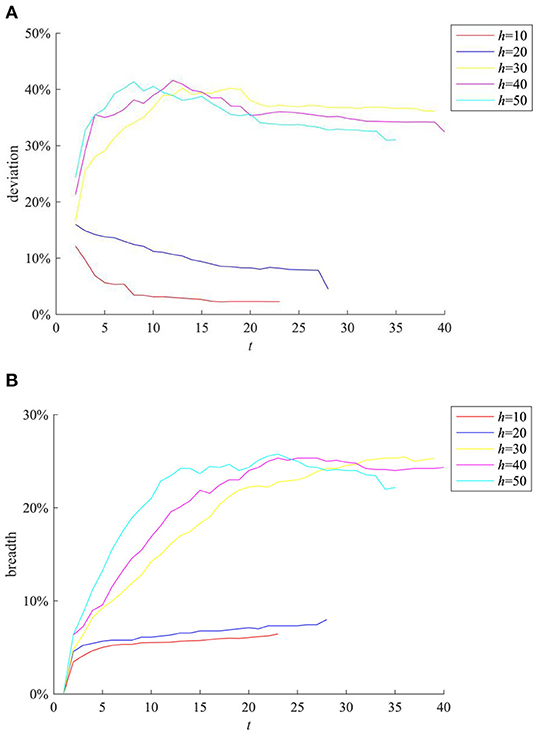
Figure 7. The impact of network structure on rumor evolution process. (A) Entire network information content deviation. (B) Rumor diffusion range.
It can be seen from Figures 7A,B that when h = 20, the information content deviation of the entire network and the rumor diffusion range are higher than the case of h = 10. When h = 30, the information content deviation of the entire network exceeds 30%, and the rumor diffusion range also exceeds 20%. It can be seen that the increase of h can promote the rumor diffusion. This is mainly because when h is small, the average degree of network nodes is low, and the connection between individuals is weak, which makes the information diffusion channel blocked, resulting in small rumor diffusion range. With the increase of h, the average network degree of nodes increases, the connection among individuals is strengthened, and the information interactions among individuals become more frequent, which creates conditions for the rumor diffusion. However, it is easy to find that when h ≥ 30, the increase of h no longer expands the entire network information content deviation of the entire network and the rumor diffusion range, indicating that the average network degree of nodes has a peak in the influence of rumor diffusion range.
The Impact of μc on Rumor Evolution Process
The trust threshold reflects the cautious of an individual treating external information, and its value will affect his/her reception of external information. Here we select the cases where the mean value of individual trust threshold μc(μc = ∑ (ci)/N) is 0.1, 0.3, 0.5, 0.7, 0.9, respectively, for comparison, and the results are shown in Figure 8.
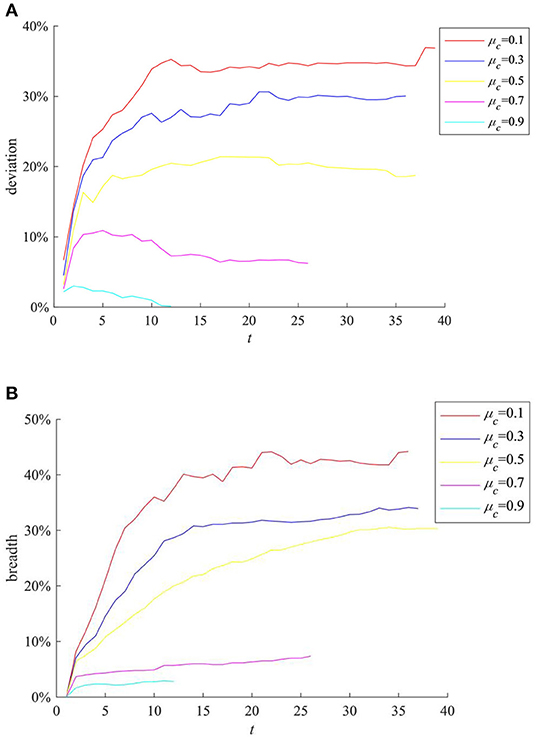
Figure 8. The impact of μc on rumor evolution process. (A) Information content deviation. (B) Rumor diffusion range.
It can be seen from Figures 8A,B that with the increase of μc, the entire network information content deviation and the rumor diffusion range gradually decrease. This is because the increase in the average trust threshold means that the information recipients generally reduce their trust in the network, and they are increasingly inclined to refuse to information from the outside world, resulting in more obstacles for information diffusion, making it impossible for further diffusion.
Analysis of Rumor Control Strategy
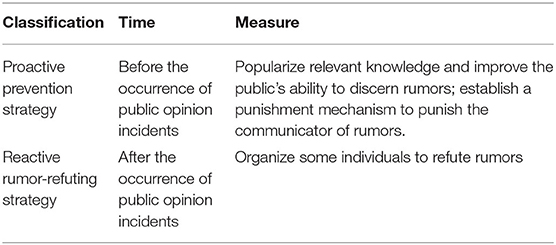
In this section, according to the time and means of implementing the rumor control strategies, they are divided into proactive prevention and reactive rumor refuting ones, as shown in Table 3. Among them, the prevention strategy refers to the preventive strategy taken before the occurrence of public opinion incidents. The reactive strategy refers to the refuting strategy taken after the occurrence of the rumors. Here, the effects of the two types of strategies are compared and analyzed through simulation experiments.
The current academic research on rumor control mainly focuses on how to reduce the impact of rumors, and rarely considers the negative impact of rumor control strategies, which leads to insufficient network activity. Currently, the social network has become an important channel for the media to release information, the public to obtain information, and the public to seek appeals. Insufficient network activity will prevent the important information from being diffused, and it will not satisfy the public's right to know public events. Based on this, the number of individuals participating in information interaction at different time moments is calculated as a measure of network activity to reflect the changes in network activity under different control strategies, so as to more comprehensively compare and analyze the positive and negative effects of different rumor control strategies.
Proactive Prevention Strategy
According to the different implementation methods of the strategy, the proactive prevention strategy is further divided into the knowledge popularization strategy and the punishment and restriction strategy.
(1) Knowledge popularization strategy
The knowledge popularization strategy refers to the one to restrict rumor diffusion by popularizing relevant knowledge in the field to individuals before the occurrence of public opinion events in a certain field. Here, the average knowledge reserves of network individuals reflect the implementation of the knowledge popularization strategy. They are set to follow the Poisson distribution with the mean λ of 1, 2, 3, 4, and 5, respectively, and the rumor diffusion when individuals have different levels of knowledge reserves is compared. The results are shown in Figure 9.
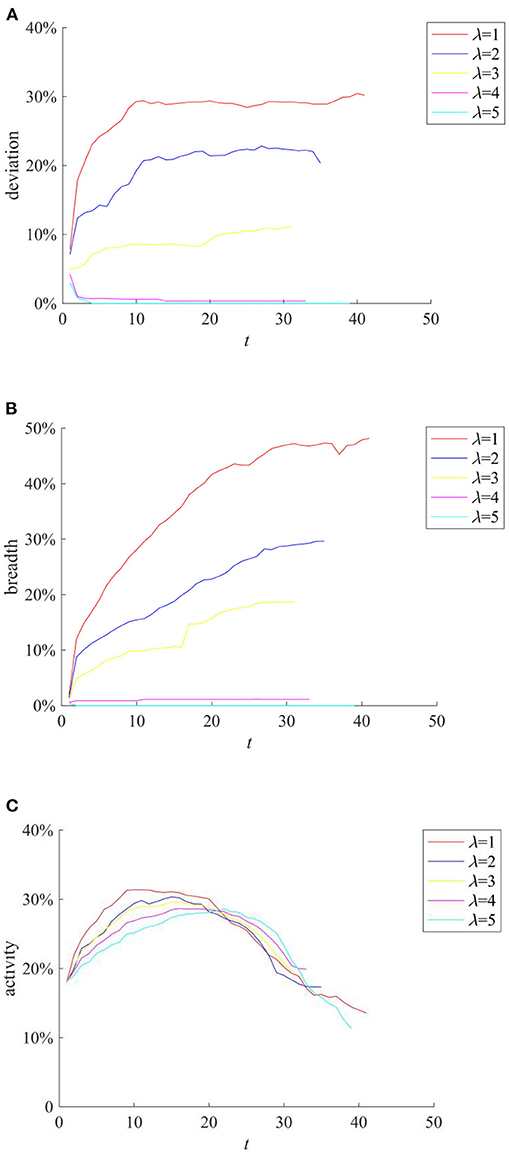
Figure 9. The effects of different knowledge popularization strategies. (A) Entire network information content deviation. (B) Rumor diffusion range. (C) Network activity.
It can be seen from Figures 9A,B that with the increase of λ, the higher level of individual knowledge reserves in the network represents the greater probability of the authentic identification information and greater possibility of rejecting rumors, reducing the scale of information content deviation and rumor diffusion range. It can be seen that adopting knowledge popularization strategies can effectively reduce the influence of rumors. In addition, it can be seen from Figure 9C that with the increase of λ, the peak value of network activity decreases, but its descend range is smaller. This is because when individual knowledge reserves are small, the public knows less about the causes and consequences of public events. In order to satisfy their own curiosity, they often trigger large-scale discussions on the Internet. However, with the increase of individual knowledge reserves, individuals can reason and derive the causes and consequences of events based on their own knowledge, which reduces the discussion on the network, and decreases network activity.
(2) Punishment and restriction strategy
Punishment and restriction strategy refers to the establishment of online code of conduct and punishment mechanism before the occurrence of public opinion incidents to restrict the individual behavior and rumor diffusion. Here we compare the rumor diffusion when the government punishment is 0.1, 0.3, 0.5, 0.7, and 0.9. The results are shown in Figure 10.
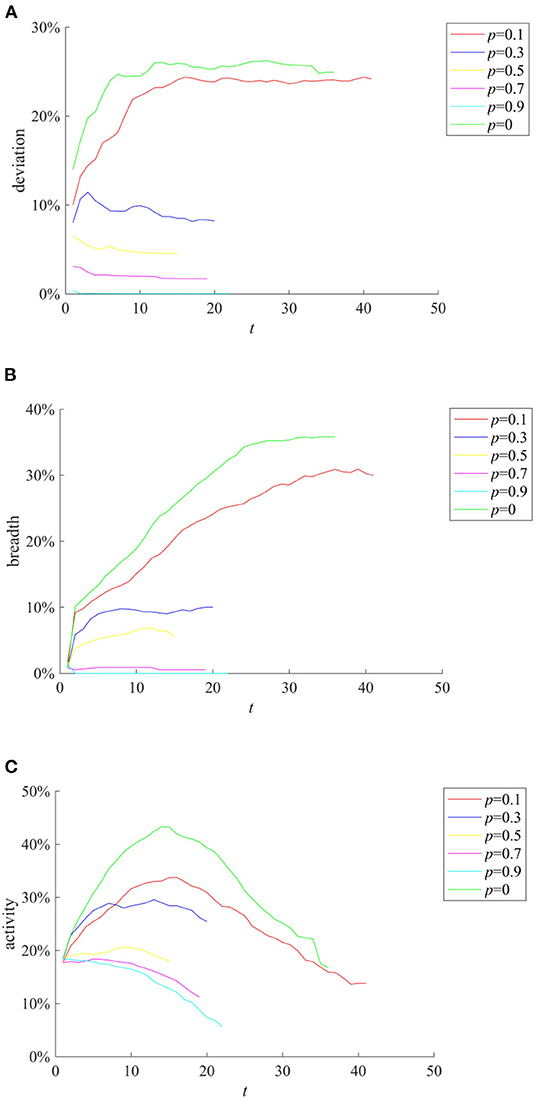
Figure 10. The effects of different punishment and restriction strategies. (A) Entire network information content deviation. (B) Rumor diffusion range. (C) Network activity.
It can be seen from Figures 10A–C that as the punishment p increases, the entire network information content deviation range, the rumor diffusion, and the network activity decrease accordingly. In addition, when p = 0.1, the information content deviation has decreased, but it is close to the situation when there is no punitive measures. When p is equal to 0.5, 0.7, and 0.9, respectively, although the information content deviation and the rumor diffusion range are very low, the network activity is insufficient. In contrast, when p = 0.3, while avoiding low network activity, the entire network information content deviation and the rumor diffusion range are well-controlled.
(3) Analysis of combined proactive strategies
After analyzing the above two proactive strategies separately, this section analyzes the different combined effects of the two strategies. Here, set p equal to 0.1, 0.3, 0.5, 0.7, 0.9, and λ equal to 1,2 3, 4, and then combine p and λ with different values to form different strategy combinations, and compare the effects of different strategy combinations at t = 1, 15, 30, and 45. The results are shown in Figures 11–13.
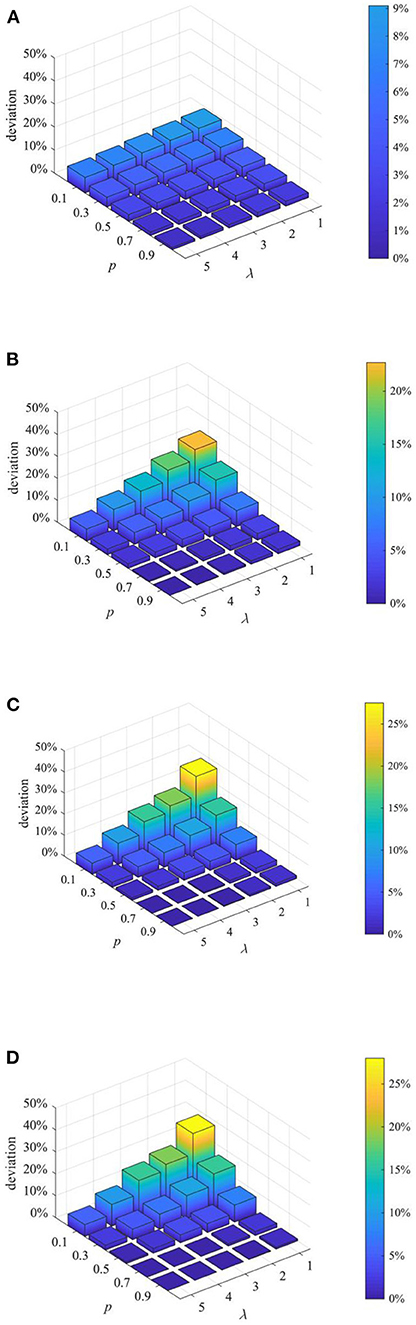
Figure 11. The entire network information content deviation under different strategy combinations. (A) t = 1. (B) t = 15. (C) t = 30. (D) t = 45.
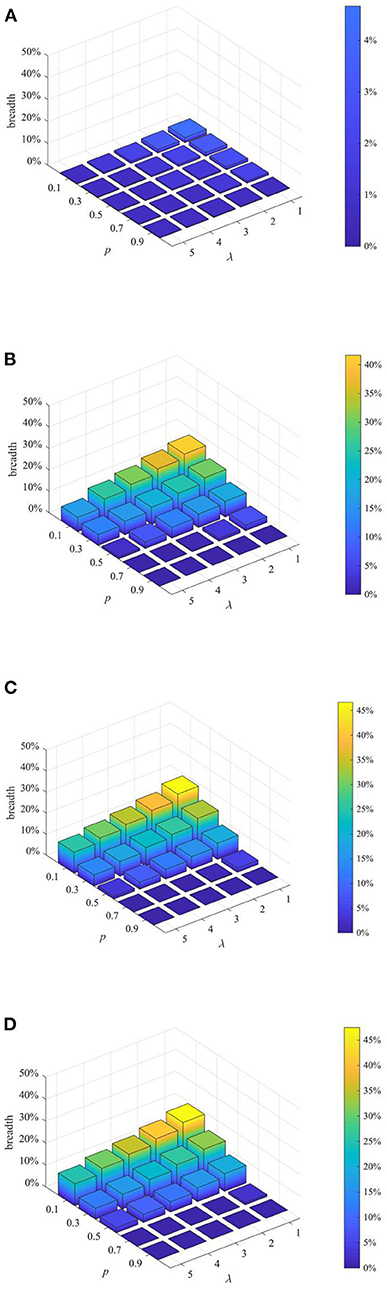
Figure 12. Rumor diffusion range under different strategy combinations. (A) t = 1. (B) t = 15. (C) t = 30. (D) t = 45.
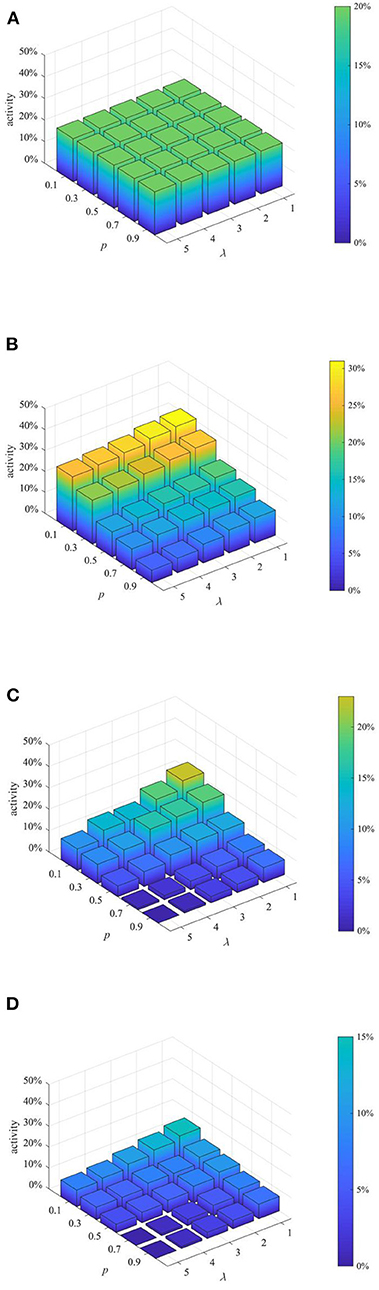
Figure 13. Network activity under different strategy combinations. (A) t = 1. (B) t = 15. (C) t = 30. (D) t = 45.
It can be seen from Figures 11–13 that with the increase of p and λ, the entire network information content deviation, the rumor diffusion range, and the network activity are continuously reduced. In addition, when λ is fixed, with the increase of p, the information content deviation, network activity and the rumor diffusion will be significantly reduced. When p is fixed, with the increase of λ, the decrease in network activity will be smaller, and the rumor diffusion range will be slightly reduced. Although the information content deviation of the entire network is greatly reduced, the rate of decrease is relatively slow. It can be seen that the rumor control effect of the punishment and restriction strategy is better than that of the knowledge popularization one, but its restraining influence on the network activity is also far greater than that of the knowledge popularization strategy.
Reactive Strategy
After the rumors are formed, it is necessary to adopt a strategy of dispelling the rumors to suppress the rumor diffusion. In general, the basic idea of the rumor rejection strategy is as follows: when the rumors diffuse to a certain extent, a certain number of nodes are randomly selected as the rumor-refuting individuals, which will diffuse real information to other nodes at a certain frequency, and finally achieve the effect of suppressing the rumors.
Here, we first compare the influence of the time moment on the effect of rumor refuting strategy. Figure 14 compares the implementation effects of selecting the same number of network nodes as rumor-refuting individuals when the rumors diffusion range reaches 3, 6, 9, 12, and 15%, and disseminating rumors at the same frequency.
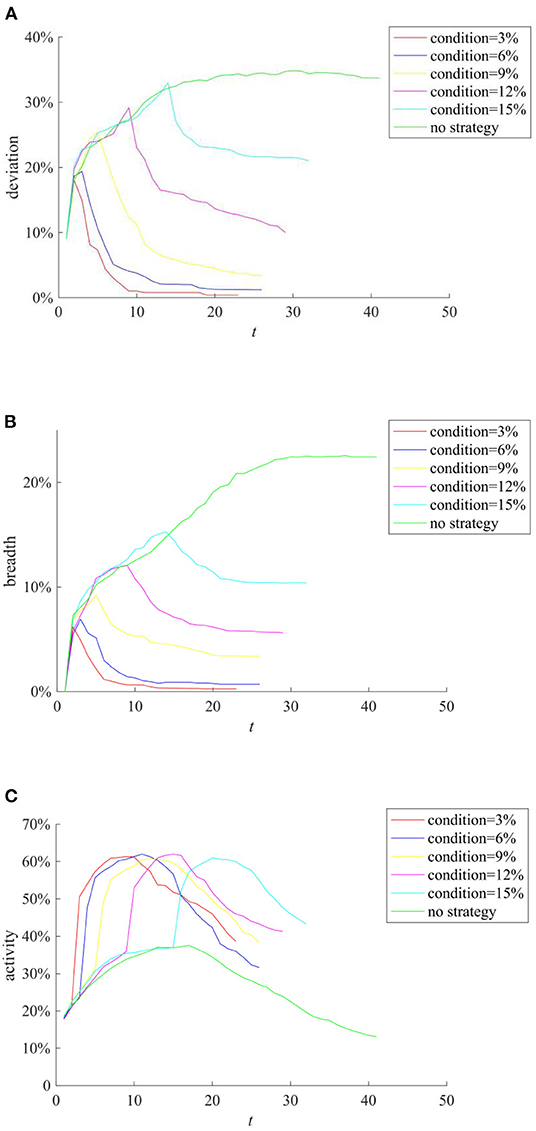
Figure 14. The influence of the time moment on the effect of rumor refuting strategy. (A) Entire network information content deviation. (B) Rumor diffusion range. (C) Network activity.
It can be seen from Figure 14 that there are significant differences between the entire network information content deviation and the rumor diffusion range under the rumor refuting strategy. After adopting rumor-refuting strategy, the entire network information content deviation and the rumor diffusion range immediately changed from a rapid rise to a rapid decline. It can be seen from Figures 14A–C that when the rumor diffusion range reaches 3 or 6%, the rumor refuting strategy can quickly reduce the influence of rumors in a short period of time, purify relevant network information content, and finally make the rumors almost disappear. Although adopting a strategy to refute rumors when the scale of rumor diffusion range reaches 9, 12, and 15% can also greatly reduce the impact of rumors, as the time moment of the strategy is postponed, the rumors have formed a certain scale and the difficulty of refuting rumors has increased. The final effect of the strategy gradually deteriorated. In addition, the adoption of rumor refuting strategy has greatly increased network activity, and has caused a new round of useful discussions on public opinion events. To sum up, after a public opinion incident occurs, the government should adopt a rumor-refuting strategy as soon as possible to minimize the impact of rumors.
In addition, during the implementation of the rumor-refuting strategy, the time interval of rumor-refuting (the time interval between two adjacent rumor-refuting behaviors) and the number of individuals that refute the rumors (the individuals that refute the rumors point to other individuals who diffuse the true information content) will affect the ultimate effect of the rumor-refuting strategy. Figure 15 compares the implementation effects of selecting 10, 20, 30, 40, and 50 network nodes as individuals to dispel rumors when the rumor diffusion reaches 10%. Figure 16 compares the implementation effect of selecting the same number of network nodes as the rumor-refuting individuals and diffusing the rumor-refuting information at intervals of 1, 2, 3, 4, and 5 when the rumor diffusion reaches 10%.
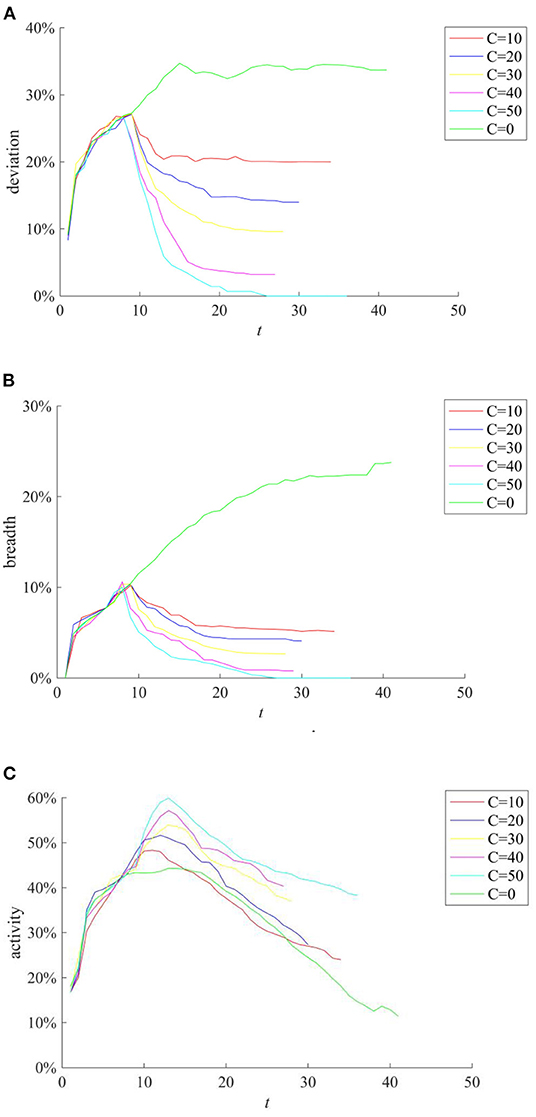
Figure 15. The effect of rumor-refuting strategies based on different rumor-refuting individuals. (A) Information content deviation. (B) Rumor diffusion range. (C) Network activity.
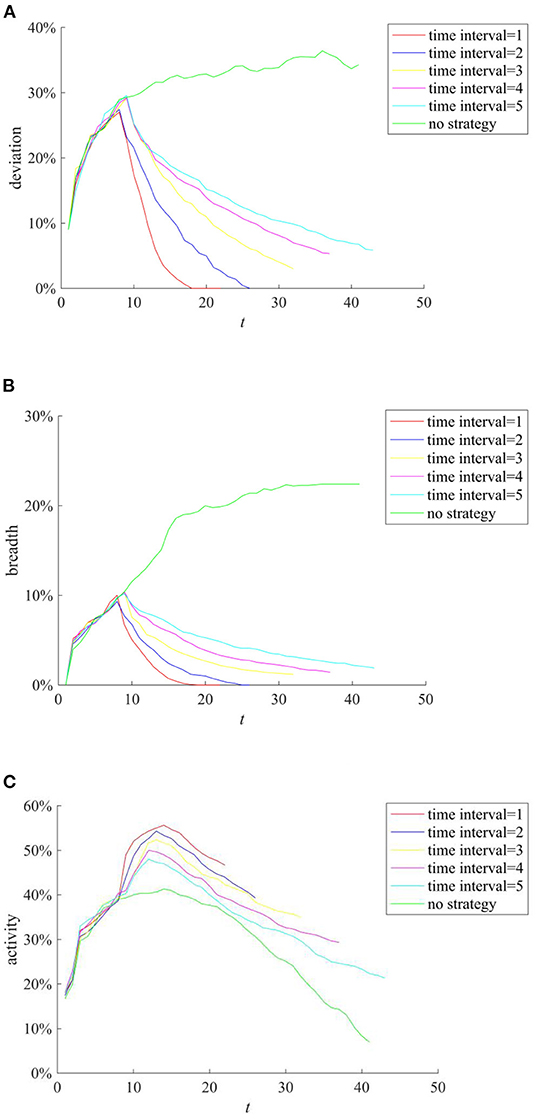
Figure 16. The effect of rumor-refuting strategies based on different rumor time refuting interval. (A) Entire network information content deviation. (B) Rumor diffusion range. (C) Network activity.
It can be seen from Figures 15A,B that with the increase of the number of rumor-refuting individuals, the scale of entire network information content deviation and rumor diffusion range has dropped significantly. In addition, it can be seen from Figures 16A,B that the shorter the time interval of refuting rumors, the more effective the rumor-refuting strategy will be. Moreover, from Figures 15C, 16C, it can be seen that the increase in the number of rumor-refuting individuals and the expansion of the time interval for rumor-refuting have significantly improved network activity.
Furthermore, considering the urgency and necessity of rumor control, it is necessary to find out the most critical factors in the process of refuting rumors. Based on this, a combined analysis of the number of rumor-refuting individuals and the time interval of rumor-refuting is conducted. Here, the numbers of rumor-refuting individuals are 10, 20, 30, 40, 50, and the time intervals of rumor-refuting are 1, 2, 3, 4, 5, and then combine in pairs to form 25 different strategies. The implementation effects of the combination at t = 1, 15, 30, and 45 are compared, and the results are shown in Figures 17–19.
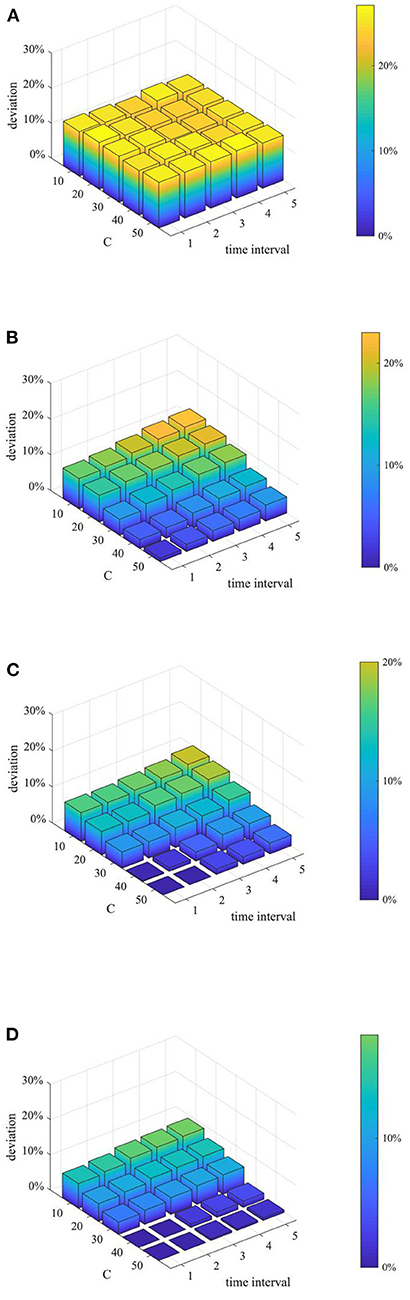
Figure 17. Entire network information content deviation based on different combination. (A) t = 10. (B) t = 20. (C) t = 30. (D) t = 40.
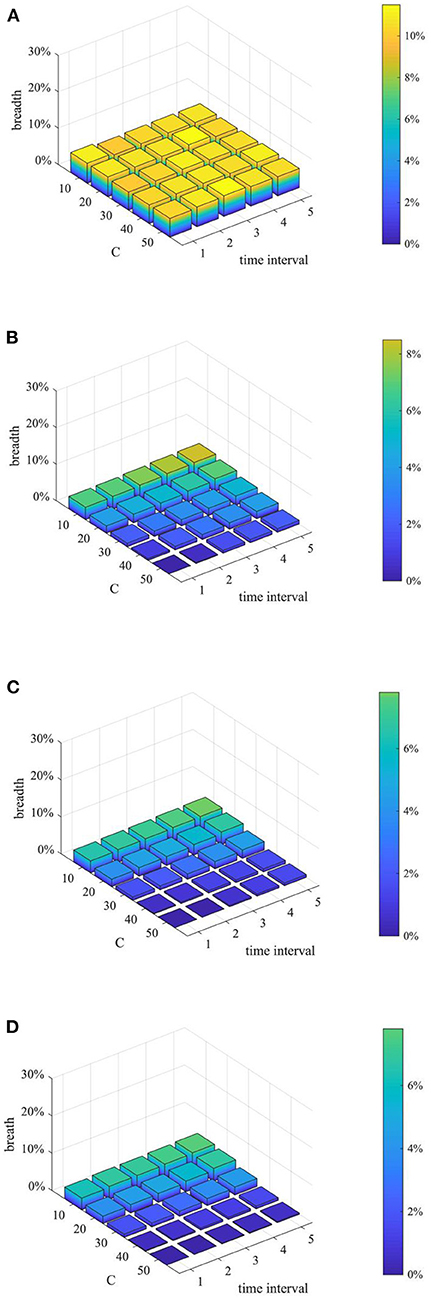
Figure 18. Rumor diffusion range based on different combination. (A) t = 10. (B) t = 20. (C) t = 30. (D) t = 40.
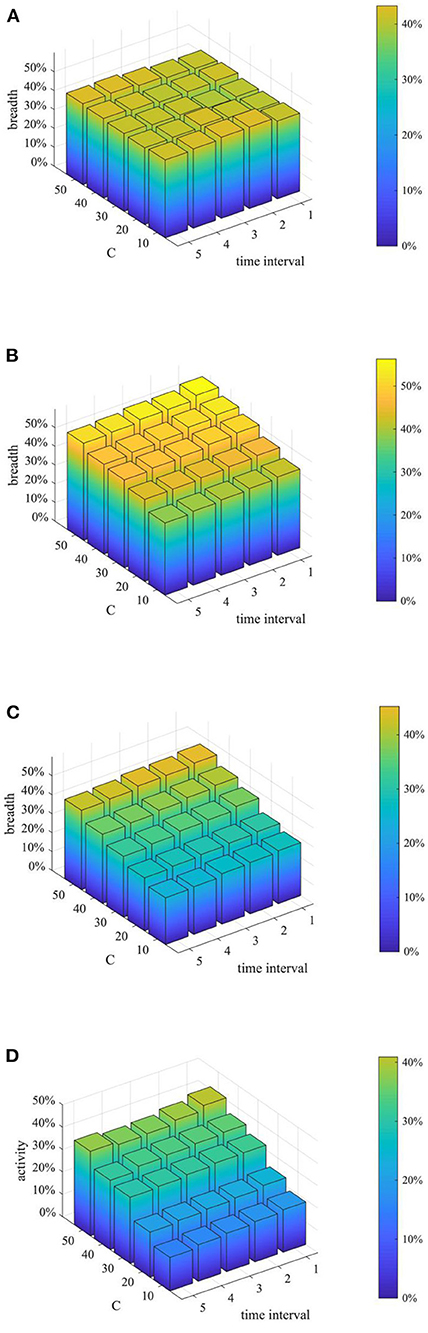
Figure 19. Network activity based on different combination. (A) t = 10. (B) t = 20. (C) t = 30. (D) t = 40.
As can be seen from Figures 17–19, when the time interval of rumor-refuting is fixed, as the number of refuting rumor individuals increases, the entire network information content deviation decreases rapidly, the rumor diffusion range is significantly reduced, and the network activity increases significantly. On the other hand, when the number of refuting rumors remains the same as the time changes, the reduction of the time interval of rumor-refuting can speed up the decline of entire network information content deviation and rumor diffusion range, but it has little effect on the final information content deviation and the rumor diffusion range, and it has no obvious effect on the improvement of network activity. This shows that when adopting a rumor-refuting strategy, more attention should be paid to the number of rumor-refuting individuals.
Analysis and Discussion
In this section, some simulation results and findings are given firstly. Subsequently, the limitations of our study are also discussed.
Simulation Results and Findings
Through simulation experiments, the influence of model parameters on the evolution of rumors is analyzed, and the following conclusions are obtained:
(1) The higher average value of the interest correlation between individuals and the event that caused the rumors represents the lower deviation between the network information content and the real information content, and the larger scale of the rumor diffusion range.
(2) Increasing the average network degree of nodes can expand the influence of rumors, but its influence on the rumor diffusion range has a peak.
(3) The higher average trust threshold of all individuals in the network represents the lower entire network information content deviation, and the smaller scale of the rumor diffusion range.
In addition, according to the implementation effects of different rumor control strategies, the following conclusions are obtained:
(1) Before a public opinion incident occurs, adopting a knowledge popularization strategy and a punishment and restriction strategy for the public can effectively minimize the information content deviation and the rumor diffusion range after the public opinion incident occurs. Besides, the rumor control effect of the punishment and restriction strategy is better than that of the knowledge popularization strategy, but its inhibitory effect on network activity is far greater than that of the knowledge popularization strategy.
(2) After a public opinion incident occurs, the government should adopt a strategy of refuting rumors as soon as possible to minimize the impact of rumors. Moreover, when adopting a rumor-refuting strategy, more attention should be paid to the number of rumor-refuting individuals.
Limitations
In this study, there are still some shortcomings in simulation analysis as follows: the BA network constructed in the simulation analysis does not consider the growth of nodes in the diffusion of sudden hot events at the initial moment. Therefore, the network structure needs to be further optimized in the follow-up.
Empirical Analysis
This section selects “Imported Food Safety Issue during the COVID-19 Pandemic” (hereinafter referred to as “Imported Food Safety”) as an example to verify the effectiveness of the SEIR-OM model.
After the outbreak of COVID-19, in order to prevent the import of the virus from abroad, General Administration of Customs People's Republic of China (GACC) has strengthened the testing of imported food. In June 2020, the COVID-19 was detected on the surface of the imported salmon cutting board at the Xinfadi Seafood Wholesale Market in Beijing, which quickly caused panic among Chinese residents, leading to intense discussions on imported food safety issue. Since then, GACC has repeatedly detected positive samples of COVID-19 virus nucleic acid on the outer packaging of imported food or on the surface of the food, which has caused heated discussions on many occasions.
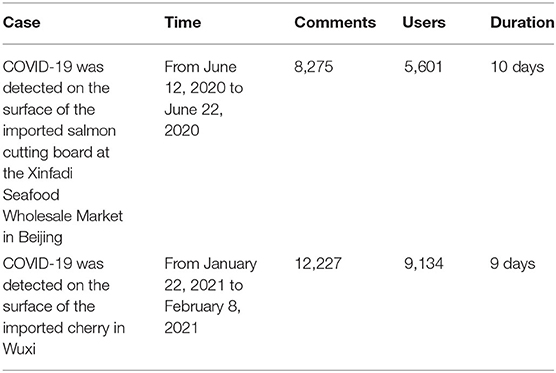
In order to analyze the diffusion of rumors in the “Imported Food Safety” incident, two incidents with a large amount of topic discussion are selected as the analysis objects based on the topic search on the Weibo platform. Firstly, the COVID-19 was detected on the surface of the imported salmon cutting board at the Xinfadi Seafood Wholesale Market in Beijing. Discussions on this incident were mainly focused on June 12, 2020–June 22, 2020. Secondly, the COVID-19 was detected on the surface of the imported cherry in Wuxi, Jiangsu Province in China on January 22, 2021. Discussions on this incident mainly focused on January 22, 2021–February 8, 2021. There are discussions about these two incidents on the Internet, such as “Eating imported food will get COVID-19” and “Eating imported food is dangerous.” In response to these remarks, many Chinese official media continues to quote expert opinions to clarify and refute rumors.
The relevant Weibo data is crawled through python, and a total of 41,351 data is obtained. The schematic diagram of the data is shown in Figure 20.
After obtaining and preprocessing the data, it is necessary to identify the content of the comments. Here, we first establish two corpus sets including rumors and truths related to “Imported Food Safety,” and then use JIEBA (32) word segmentation algorithm and word2vec algorithm to calculate the similarity between the review content and the two corpora sets one by one. If the similarities between the review content and the two corpora sets are low, it will be recognized as an irrelevant comment. If a comment is more similar to the rumor text set than the real content corpus set, it will be recognized as a rumor, otherwise it will be recognized as a truth. After removing irrelevant comments, there are 20,502 pieces of data in the two cases. Although the amount of data here is limited, according to the six-degree separation theory (33) in interpersonal relationships, the statistical results of these user data can reflect the universality of Weibo user behavior to a large extent. The data information involved in the case analysis is shown in Table 4.
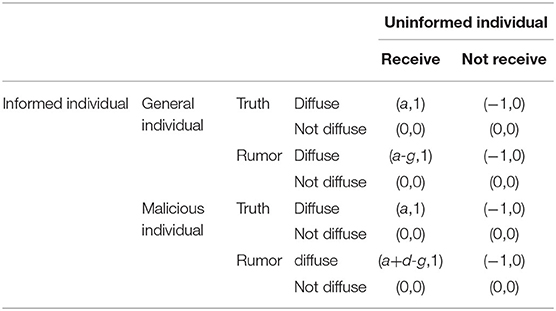
In order to verify the validity of the SEIR-OM model constructed in this article, the existing evolutionary game model is introduced and compared with SEIR-OM model. We make the following three assumptions about the evolutionary game model: (1) The individuals in the network are divided into uninformed individuals and informed individuals according to their states. (2) Only the game behavior between informed individuals and uninformed individuals is discussed in the model. (3) There are malicious individuals in the network. The rules of game gains in the model are set as follows: (1) When an informed individual chooses to diffuse information, if the uninformed individual receives the information, the informed individual will get a higher gain a (a > 1), and the uninformed individual's gain is equal to 1; (2) When an informed individual chooses to diffuse information, if the uninformed individual does not receive the information, the informed individual's gain will be damaged and become −1, and uninformed individual's gain will be 0; (3) When the informed individual does not diffuse information, the gains of both parties are 0; (4) If malicious individuals successfully diffuse rumors to uninformed individuals, they can obtain excess gains; (5) Individuals who diffuse rumors will be punished by the government, and their gains will decrease by g. According to the above rules, the gain matrix of the evolutionary game model is shown in Table 5.
In addition, the individual strategy update rules in the evolutionary game model are as follows: individual i randomly selects a neighbor individual j, and imitates the strategy of j with a certain probability, as shown in formula (19).
where Si and Sj are the strategies adopted by i and j; Pi and Pj are the cumulative gains of i and j after the game; ki, kj are the degrees of i and j; H is the maximum difference in the game gains between individuals.
Since the evolutionary game model cannot reflect the difference of information content, i.e., it cannot calculate the deviation degree of information content, the comparison content of different models only includes the rumor diffusion range and network activity. In order to make the simulation environment closer to the real situation of the two incidents, some parameters in the two models will be adjusted according to the data of different time periods: (1) According to the Pareto principle (34), 20% of the people in society will produce 80% impact, and malicious individuals play a major role in the rumor diffusion. Therefore, the proportion of malicious individuals in the two models is set to be 20%; (2) The Chinese government takes a strong management measures on online rumors, so the intensity of government punishment p is set to 0.5 in the SEIR-OM model, and the government punishment g in the evolutionary game model is set to 0.5, too; (3) On June 14, 2020, when the deviation of the online information content of the “COVID-19 was detected on the surface of the imported salmon cutting board in Beijing” reached more than 10%, the official media refuted the rumor for the first time. Therefore, in response to this incident, when the entire network information content deviation is >10%, the government adopts a rumor-refuting strategy. Similarly, for the “the COVID-19 was detected on the surface of the imported cherry in Wuxi, Jiangsu,” it is set that when the entire network information content deviation is >3%, the government adopts a rumor-refuting strategy; (4) As experts keep responding to the doubts about the safety of imported foods, the public's knowledge reserves going up. Therefore, it is assumed that the individual knowledge reserves in the SEIR-OM model obey the Poisson distribution with the mean λ is 1 and 3 in the two time periods, respectively; (5) In these two incidents, the government's time interval for rumor-refuting was 5 and 2 days, respectively. Therefore, the government's rumor-refuting time interval in the SEIR-OM model was set to 5 and 2 days, respectively; (6) Because the difficulty of diffusing rumors after the government has refuted the rumors will increase, the excess gain of malicious individuals diffusing false information will decreases. As a result, the excess gain of malicious individuals diffusing false information in the evolutionary game model before the government refuting the rumors is assumed to be 0.7, and becomes 0.3 after the government refuting the rumors. In addition, the other parameters of the SEIR-OM model are set as: μb = 0.9, μc = 0.5. The other parameters in the evolutionary game model are set as: a = 0.12, H = 5. It is assumed that the number of simulation network nodes of the two models is both 500.
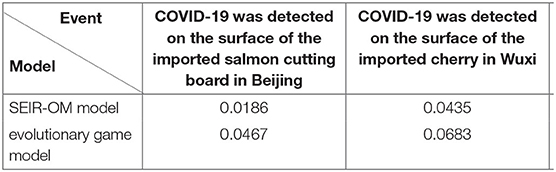
SEIR-OM model and the evolutionary game model are used to simulate the changes in the rumor diffusion in the two incidents here, and the two change curves are compared with the actual curves shown in Figure 21. In this figure, the blue line represents the rumor diffusion curve simulated by the SEIR-OM model, the red line represents rumor diffusion curve simulated by the evolutionary game model, and the yellow line represents the rumor diffusion curve based on real data. In addition, the Root Mean Square Error (RMSE) is used here to accurately reflect the error between the variation curve of the rumor diffusion range simulated by SEIR-OM model, evolutionary game model and the real data. The results are shown in Table 6.
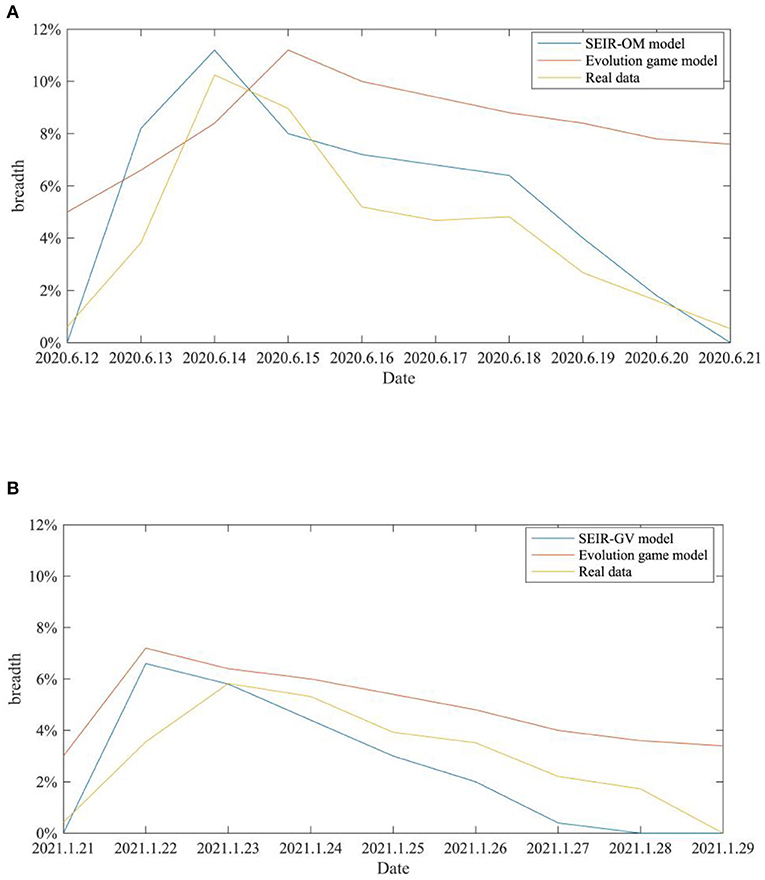
Figure 21. Comparison of the rumor diffusion ranges in two events. (A) COVID-19 was detected on the surface of the imported salmon cutting board in Beijing. (B) COVID-19 was detected on the surface of the imported cherry in Wuxi.
It can be seen from Figures 21A,B that the rumor diffusion curves simulated by the two models both show an upward trend before the government adopts the intervention strategy, and the curve simulated by the SEIR-OM model rises faster. After the government adopts the intervention strategy, the curve simulated by the evolutionary game model shows a gentle downward trend. In contrast, the curve simulated by the SEIR-OM model declines faster, and the change trend is similar to the real curve. According to Table 6, in terms of rumor diffusion, the error of the simulation results of the SEIR-OM model in the two incidents is smaller than that of the evolutionary game model, and the simulated curve is closer to the real curve, indicating that the SEIR-OM model is closer to real situation in terms of rumor diffusion.
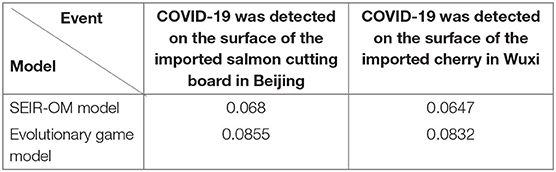
In addition, the SEIR-OM model and the evolutionary game model are used to simulate the changes in network activity in the two events and compare with the real situation shown in Figure 22. In this figure, the blue line represents the network activity curve simulated by the SEIR-OM model, the red line represents the network activity curve simulated by the evolutionary game model, and the yellow line represents the network activity curve drawn based on real data. In addition, the RMSE is used here to accurately reflect the error between the network activity curve simulated by the SEIR-OM model and the evolutionary game model and the real curve. The results are shown in Table 7.
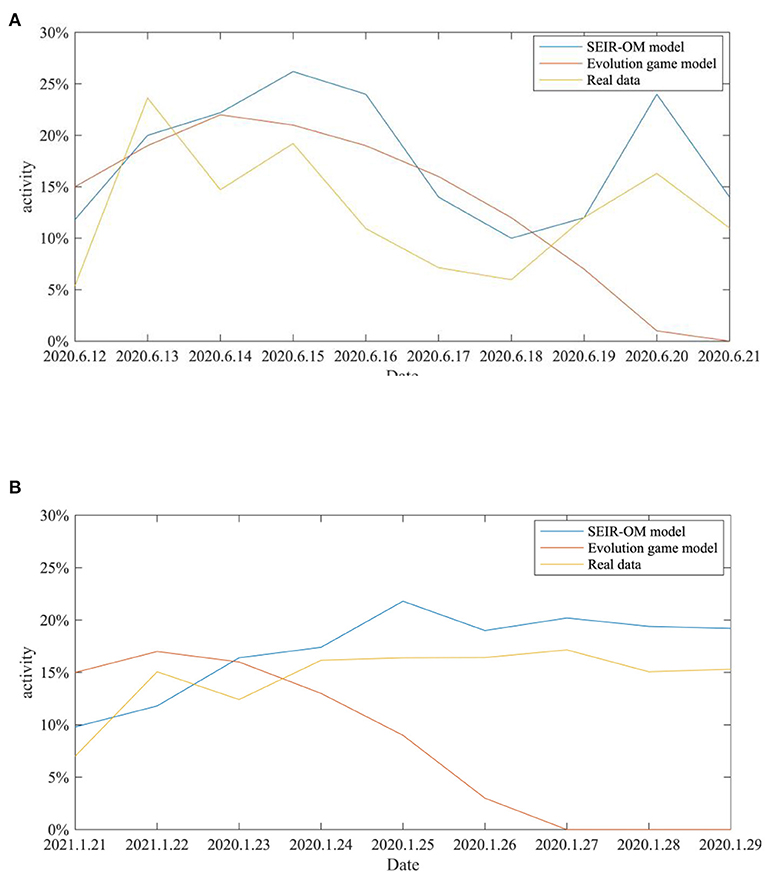
Figure 22. Comparison of the network activities in the two incidents. (A) COVID-19 was detected on the surface of the imported salmon cutting board in Beijing. (B) COVID-19 was detected on the surface of the imported cherry in Wuxi.
From Figures 22A,B, it can be seen that the network activity curves of the two events simulated by the evolutionary game model both show an upward trend, and then a downward trend after the government adopts an intervention strategy, and the rate of decline keeps accelerating. In contrast, due to the different frequency of government refuting rumors, the two curves simulated by the SEIR-OM model have certain differences. The simulated network activity curve for the “COVID-19 was detected on the surface of the imported salmon cutting board in Beijing” event has two peaks, while the simulated network activity for the other incident remained stable at about 20% after the government frequently refuted rumors. After comparing the actual curve, it is easy to find that the curve simulated by the SEIR-OM model is closer to the actual curve, indicating that the SEIR-OM model is closer to the real situation in terms of network activity.
In addition, in order to reflect the effectiveness of the SEIR-OM model in terms of entire network information content deviation, this curve simulated by the SEIR-OM model is compared with the actual curve, and the result is shown in Figure 23. In Figure 23, the blue line represents the information content deviation curve simulated by the SEIR-OM model, and the red line represents the information content deviation curve drawn based on real data.
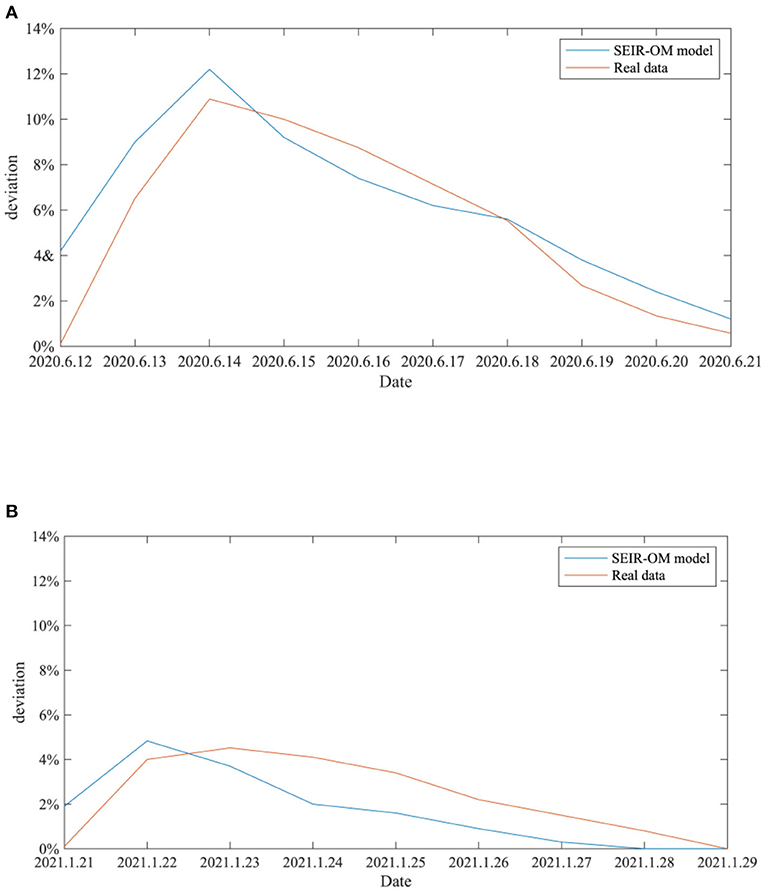
Figure 23. Comparison of entire network information content deviations in two events. (A) COVID-19 was detected on the surface of the imported salmon cutting board in Beijing. (B) COVID-19 was detected on the surface of the imported cherry in Wuxi.
It can be seen from Figure 23 that in terms of entire network information content deviation, although the curve simulated by the SEIR-OM model is different from the real data curve, the trend of the two is similar. Therefore, it shows that SEIR-OM model performs well in the entire network information content deviation.
Conclusions
This article integrates individual heterogeneity factors into the SEIR model, and designs an individual state transition mode at first. Subsequently, based on trust theory and information asymmetry theory, it establishes an individual information interaction mode, and constructs an improved SEIR model named SEIR-OM model. Then the diffusion process of rumors and the implementation effects of different rumor control strategies are simulated and analyzed. Finally, the article verifies the rationality and effectiveness of the SEIR-OM model through the real case from the imported food safety issue during the COVID-19 Pandemic.
However, this article still has the following shortcomings, which need further study:
(1) The BA network constructed in the article only considers the exit of the interconnection among nodes, but does not consider the growth of nodes in the diffusion of sudden hot events at the initial moment. Therefore, the network structure needs to be further optimized in the follow-up.
(2) Rumors in the constructed model are transmitted through random pairwise information interaction between the Internet and the people. In reality, a netizen can send the information to a designated person, or send it in groups to his friends or strangers. Therefore, it is necessary to consider a variety of forms of private information transmission on the Internet, such as group sending, and directional sending.
Data Availability Statement
The data used to support the findings of this study are available from the corresponding author upon request.
Author Contributions
TC described the proposed framework and wrote the whole manuscript. JR implemented the simulation experiments. JY collected data. GC revised the manuscript. All authors read and approved the final manuscript.
Funding
This research was supported by the National Social Science Foundation of China (20BTQ059).
Conflict of Interest
The authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher's Note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
References
1. Zhang Y, Zhu J. Stability analysis of I2S2R rumor spreading model in complex networks. Phys A Stat Mech Appl. (2018) 503:862–81. doi: 10.1016/j.physa.2018.02.087
2. Huang J, Jin X. Preventing rumor spreading on small-world networks. J Syst Sci Compl. (2011) 24:41–8. doi: 10.1007/s11424-011-8303-1
3. Jiang P, Yan X. A quantitative model for the spread of online information. Quality Quantity. (2019) 3:1981–2001. doi: 10.1007/s11135-019-00851-3
4. Zhou L, Liu Z, Li B. Influence of network structure on rumor propagation. Phys Lett A. (2007) 368:458–63. doi: 10.1016/j.physleta.2007.01.094
5. Moreno Y, Pastor-Satorras R, Vespignani A. Epidemic outbreaks in complex heterogeneous networks. Euro Phys J B Condensed Matter Complex Syst. (2001) 26:521–9. doi: 10.1140/epjb/e20020122
6. Zhang Y, Xu J, Wu Y. A fuzzy rumor spreading model based on transmission capacity. Int J Modern Phys C. (2018) 29:1850012. doi: 10.1142/S0129183118500122
7. Fernández-Domingos E, Loureiro M, Alvarez-López T, Burguillo JC, Covelo J, Peleteiro A, Byrski A. Emerging cooperation in n-person iterated prisoner's dilemma over dynamic complex networks. Comput Informatics. (2017) 36:493–516. doi: 10.4149/cai_2017_3_493
8. Li D, Ma J, Tian Z, Zhu H. An evolutionary game for the diffusion of rumor in complex networks. Phys A Stat Mech Appl. (2015) 433:51–58. doi: 10.1016/j.physa.2015.03.080
9. Mojgan A, Behrouz TL, Manshaei MH. An evolution game model for analysis of rumor propagation and control in social networks. Phys A Stat Mech Appl. (2019) 523:21–39. doi: 10.1016/j.physa.2019.01.147
10. Comin CH, Costa LD. Identifying the starting point of a spreading process in complex networks. Phys Rev E. (2011) 84:056105. doi: 10.1103/physreve.84.056105
11. Ma LL, Ma C, Zhang HF, Wang BH. Identifying influential spreaders in complex networks based on gravity formula. Phys A Stat Mech Appl. (2016) 451:205–12. doi: 10.1016/j.physa.2015.12.162
12. Pallis G. Gelling, and melting, large graphs by edge manipulation. Comput Rev. (2013) 54:500–1. doi: 10.1145/2396761.2396795
13. Yuan J, Zhang R, Tang J, Hu R, Li H. Efficient and effective influence maximization in large-scale social networks via two frameworks. Phys A Stat Mech Appl. (2019) 526:120966. doi: 10.1016/j.physa.2019.04.202
14. Zhang Y, Xu J, Wu Y. A rumor control competition model considering intervention of the official rumor-refuting information. Int J Modern Phys C. (2020) 31:2050123. doi: 10.1142/S0129183120501235
15. Zhang Y, Xu J. A mixture dynamical model considering competition and predation mechanism between rumor and rumor-refuting information. IEEE Access. (2020) 99:1. doi: 10.1109/ACCESS.2020.3047934
16. Li MY, Graef JR, Wang L, Karsai J. Global dynamics of a SEIR model with varying total population size. Math Biosci. (1999) 160:191–213. doi: 10.1016/S0025-5564(99)00030-9
17. Zhang J, Ma Z. Global dynamics of an SEIR epidemic model with saturating contact rate. Math Biosci. (2003) 185:15–32. doi: 10.1016/S0025-5564(03)00087-7
18. Gu B. Forecast and analysis of COVID-19 epidemic based on improved SEIR model. J Phys Confer Ser. (2021) 1802:042050. doi: 10.1088/1742-6596/1802/4/042050
19. Xu C, Yu Y, Yang QC, Lu Z. Forecast analysis of the epidemics trend of COVID-19 in the United States by a generalized fractional-order SEIR model. Nonlinear Dyn. (2020) 101:1621–34. doi: 10.1101/2020.04.24.20078493
20. McCroskey JC, Baer JE. Willingness to communicate: the construct and its measurement. Commun Apprehens. (1985) 71:11.
21. Zheng C, Su X, Liu X. Analysis model on online public opinion for emergency based on the stakeholder theory. J Intell. (2015) 34:71–75. doi: 10.3969/j.issn.1002-1965.2015.04.014
22. Lu L, Chen D, Zhou T. The small world yields the most effective information spreading. New J Phys. (2011). 13:123005. doi: 10.1088/1367-2630/13/12/123005
23. Hu R, Deng X. A trust problem study on internet interpersonal interaction. Document Information Knowl. (2005) 106:98–101. doi: 10.13366/j.dik.2005.04.028
24. Kim G, Shin BS, Lee HG. Understanding dynamics between initial trust and usage intentions of mobile banking. Information Syst J. (2009) 19:283–311. doi: 10.1111/j.1365-2575.2007.00269.x
25. Wu GH, Hu XR, Wu YH. Effects of perceived interactivity, perceived web assurance and disposition to trust on initial online trust. J Comput Mediated Commun. (2010) 16:11–26. doi: 10.1111/j.1083-6101.2010.01528.x
26. Aral S, Walker D. Tie strength, embeddedness, and social influence: a large-scale networked experiment. Manage Sci. (2014) 60:1352–70. doi: 10.1287/mnsc.2014.1936
27. Kuang W, Guo Y. A study of the communicating and digesting rumors in microblog era. J Int Commun. (2012) 34:64–9. doi: 10.13495/j.cnki.cjjc.2012.02.015
28. Bernstein J, Stevens RA. Public opinion, knowledge, and Medicare reform. Health Affairs. (1999) 18:180–93. doi: 10.1377/hlthaff.18.1.180
29. Petersen L. Forecast error information and heterogeneous expectations in learning-to-forecast experiments. Discussion Papers. (2014) 17:109–37. doi: 10.1108/S0193-230620140000017004
30. Chen T, Yin X, Yang J, Cong G, Li G. Modeling multi-dimensional public opinion process based on complex network dynamics model in the context of derived topics. Axioms. (2021) 10:270. doi: 10.3390/axioms10040270
31. Barabási AL, Albert R. Emergence of scaling in random networks. Science. (1999) 286:509–12. doi: 10.1126/science.286.5439.509
32. Chen T, Peng L, Yang J, Cong G, Li G. Evolutionary game of multi-subjects in live streaming and governance strategies based on social preference theory during the COVID-19 pandemic. Mathematics. (2021) 9:2743. doi: 10.3390/math9212743
33. Harvey H, Benjamin S, Susan T. The pareto principle. J Am Coll Radiol. (2018) 15:931. doi: 10.1016/j.jacr.2018.02.026
Keywords: individual heterogeneity, rumor diffusion, SEIR-OM model, rumor control, COVID-19 pandemic
Citation: Chen T, Rong J, Yang J and Cong G (2022) Modeling Rumor Diffusion Process With the Consideration of Individual Heterogeneity: Take the Imported Food Safety Issue as an Example During the COVID-19 Pandemic. Front. Public Health 10:781691. doi: 10.3389/fpubh.2022.781691
Received: 23 September 2021; Accepted: 31 January 2022;
Published: 07 March 2022.
Edited by:
Xenia Gonda, Semmelweis University, HungaryReviewed by:
Hai Wang, Saint Mary's University, CanadaDongxu Gao, University of Portsmouth, United Kingdom
Copyright © 2022 Chen, Rong, Yang and Cong. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY). The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Guodong Cong, cgd@mail.zjgsu.edu.cn
 Tinggui Chen
Tinggui Chen Jingtao Rong
Jingtao Rong Jianjun Yang
Jianjun Yang Guodong Cong4*
Guodong Cong4*